Archive for July 2023
SIGNAL- And Why .GOV Hates It

A Security Briefing
Part of working for a large company is that you sometimes get protesters- environmentalists, Antifa, BLM and their ilk. And the large company I work for takes security seriously, and monitors for upcoming protests, and makes corresponding changes in access to facilities, monitors perimeter security of the campus, works with local law enforcement, and even hires former .gov employees to manage those security efforts. By these circumstances, I happened to attend a security briefing last month, regarding upcoming protests, given by a retired FBI manager, who apparently managed a couple of different offices on the East Coast.
The lecture was pretty standard stuff, all considered, but there came a part of the presentation when he was discussing the security efforts for monitoring said groups. First bullet-point was that they used the app known as “Signal.” He went further to explain that they had no way to crack it, no matter what they tried, so they didn’t even bother to. Second point was that the work-around was to get infiltrators into said organizations, who (unlike the FBI agents who instigated the Governor Whitmer kidnapping “plot”) would pretend to be loyal supporters, always supporting the cause, mouthing the platitudes but otherwise not doing anything to arouse suspicion that the insiders were actually moles. They would do what was necessary to become part of all key leaderships comms channels on Signal, so the FBI could have a direct pipeline to all communications and planning efforts.

At one point he was flat-out laughing, saying that they had more agents inside the leadership comms channels than actual members of the respective groups, and they didn’t have a clue.
This presentation, and other discussions, started me down the rabbit-hole, to learn more about the actual .gov surveillance efforts of groups that might pose a threat the .gov agenda. It also made me question why Signal was considered “unbreakable” to the FBI (or more accurately, the NSA), and whether this was in fact true.
And finally, it made me realize that everyone needs to understand this subject, so as to have secure, PRIVATE communications, and why it matters.
BIG BROTHER IS WATCHING…
To begin with, everything you do using the internet or cell phones, is recorded and stored at NSA data centers, like the Utah one below:

Now, you may say, “what do I care, I’m not doing anything illegal!” The problem is that Joe Biden (spit!) has designated that anyone who doesn’t toe the line- especially on subjects such as the Afghanistan withdrawal, the Russia/Ukraine conflict, COVID or stolen elections- is a domestic terrorist, and is subject to prosecution. That means if they pick you out of the crowd of people discussing these subjects – for any reason or no reason at all- you have no rights. NONE. In summary, anyone who the government targets can expect no better treatment than the detainees of Gitmo. This is why the J6 defendants are horribly treated, and railroaded in sham trials; they have no rights.
According to the ACLU,
The NSA intercepts and copies private communications in bulk while they are in transit, and then searches their contents using tens of thousands of keywords associated with NSA targets. These targets, chosen by intelligence analysts, are never approved by any court, and the limitations that do exist are weak and riddled with exceptions.
This is done as part of Section 702 of the Foreign Intelligence Surveillance Act, or FISA. The operational program is called “Prism,” and was revealed by Edward Snowden in 2013.

This is possible because computer memory is cheap; a 20 Terabyte computer hard drive can be had for $360 currently at Amazon. The US government has taken advantage of the cheap memory, and built multiple NSA spy data centers in Hawaii, Colorado, Texas, Georgia, and Maryland, all interconnected by dedicated fiberoptic lines in a single, secure data cloud. The data-storage capabilities of these facilities are staggering, as this article details of the Utah facility:
This data-storage facility for the US intelligence community is designed to store data estimated at over a zettabyte, though its actual capacity is classified. Its purpose is to support the Comprehensive National Cybersecurity Initiative. A zettabyte (ZB) is 1,000 exabytes (EB). Each EB is equal to 1,000 petabytes (PB). A PB is equal to 1,000 terabytes (TB). The average personal computer today has a capacity of 1 TB with a ZB of data representing 100 million personal computers’ data capacity.
Additionally, the total amount of data created, captured, copied, and consumed globally is forecasted to increase rapidly, from 64 ZB in 2020 to more than 180 ZB by 2025—a far cry from the 2 ZB created in 2010.
How Are Large Amounts of Data Managed?
The huge amount of data can only be searched by the powerful, water-cooled HPE/Cray supercomputers at the data center. All these systems require 65 megawatts of electricity, costing about $40 million per year. The facility is estimated to use 1.7 million gallons of water per day for cooling both the supercomputers and the servers that store the data on solid-state drives. Solid-state drives have no moving parts and use a fraction of the power and water for cooling that spinning-disk hard drives require.
The high-availability, fault-tolerant system has no single point of failure. Data is striped across virtual disk arrays and mirrored for instant failover.
In the article, is a key aspect of about the NSA spy data centers:
“Redundant ping, power, and pipe guarantee availability of the information to or from any device, with 256-bit advanced encryption standard (AES) on the fly and at rest, with permission, providing protection for all data. It would take hundreds of years for the mighty Cray system to break a single instance of 256 AES encryption.” [emphasis added]
HOW many years, you might ask?
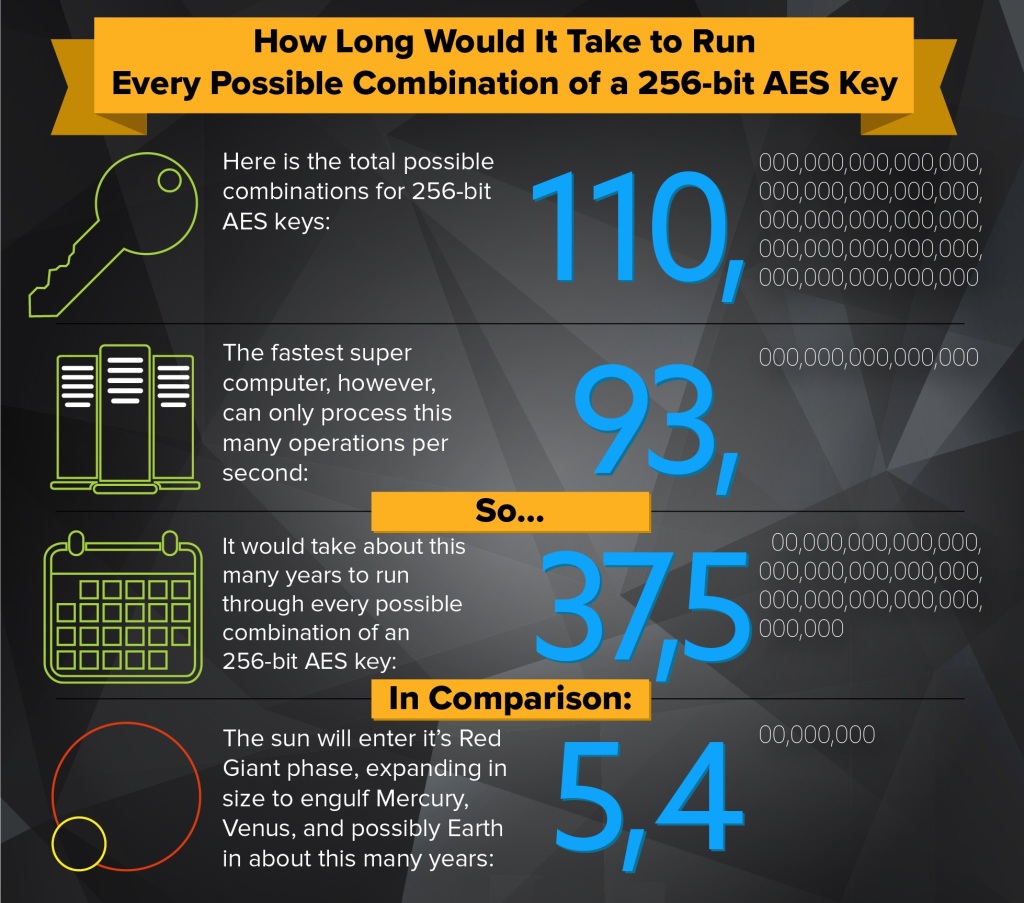
This is why .GOV uses AES-256 bit encryption for their own completely secure communications.
NSA Data Collection and Storage Limitations
The data collected by the NSA (and used by the FBI for domestic surveillance) is stored for up to one year. Despite the 1-year limitation, the amount of data hoovered-up is simply too massive for humans to meaningfully analyze, to make actionable intelligence of; this is the domain for AI-driven systems to interconnect individual data points to turn into a comprehensible picture. But even AI systems have their limits, due to required compute power and bandwidth, and so they are focused on to targets (individuals) who somehow gain the attention of the Federal government, for whatever reason.
Once a target is designated, all data gathered on that person for the past year is assembled, and analyzed. Then everyone you have communicated with, in any way, is designated a target, and all of their data is gathered and analyzed. And everyone they communicated with, in any way, is designated a target, and the same thing happens. This is the “Two-Hop Rule,” as the ACLU again describes:
If, for example, a surveillance target has talked to 200 different people in the last 18 months (a low estimate based on our informal sampling), also if each of who 200 people has including called or being called via 200 different people, when a two-hop request would dry skyward records relations to 40,000 people. And it only gets worse if ready of the numbers in the first hop belongs to a high-volume caller—like a pizza shop, an advertise company, or a hospital.
It is painfully obvious point that the US government is at war with any Americans who don’t obey. It is equally obvious that the US government relies almost exclusively on electronic intelligence, or ELINT. The store all data for future use; as soon as they notice you for committing a crime, or perhaps because you speak out to vocally against the current agenda, they pull that data, and prosecute you for a crime, whether you committed one or not.
The ONLY way to stop the government from scooping up you and everyone you know, is to use encrypted communications.
There is only one option: Signal. Signal messages are encrypted with the Signal Protocol (formerly known as the TextSecure Protocol). The protocol combines the Double Ratchet Algorithm, prekeys, and an Extended Triple Diffie–Hellman (X3DH) handshake. It uses Curve25519, AES-256, and HMAC-SHA256 as primitives.
In this article, “Is Signal safe? We asked security experts about the messaging app and your data,” several points out that “the most important privacy tool on Signal is end-to-end encryption…. which ensures that no one (not even Signal) can intercept and read your messages… Signal’s encryption, in particular, is powered by the app’s own open source Signal Protocol and adds an additional layer of security to almost every communication you hold over the app, from one-on-one messages and group chats to voice calls, video calls and even stickers… ”
This would be the AES-256 encryption that our most powerful computers could not break for hundreds of years, for a single Signal message. Essentially, if you use Signal as your only means of communication, within 12-18 months, the government no longer has any means of recording your comms, and the old data is too stale to be of any use. For this reason alone, it is foolish to use any other communications platform, whether for voice, text or email.
Further from the same article,
“Out of the three apps, Signal has the best reputation for security and privacy using published encryption that has been thoroughly scrutinised and without any incentive to capture your personal information”, said Searchlight Security CTO and co-founder, Dr. Gareth Owenson.
“WhatsApp is safe in that it uses the same secure encryption as Signal but is owned by Facebook – a company which has historically monetised personal information (principally for advertising). WhatsApp has recently come under criticism for attempting to expand the amount of data shared with Facebook”.
Telegram has a more trustworthy reputation than WhatsApp and offers more features than Signal, but this has earned the app some unsavoury users.
“Telegram has a reputation as a secure messaging app but this is largely due to the feature set it offers rather than the strong encryption”, explained Dr. Owenson.
“Research by Royal Holloway recently found vulnerabilities in the cryptography used by Telegram. Telegram is also popular amount darkweb criminals and other malicious actors due to its perceived security”.
RECAP
To summarize the revelations from the retired FBI agent and my subsequent month of research, here are my take-aways regarding Signal:
- Due to its end-to-end 256-bit dynamic encryption, Signal is unbreakable with current technology, for texts and voice or video calls. There’s no way around this for .gov actors. Obviously .GOV actors do not advertise this fact…
- The Signal servers and organization themselves cannot break the encryption of any messages any more than .gov can.
- .Gov demands of Signal for user data will only tell the last time a particular user logged in, nothing more, because the system is purposefully built that way.
- All electronic transmissions- including Signal- will be captured by the NSA spy data centers. However, with insufficient technology for many years- possibly decades – away from being able to crack even one Signal message, all they’ll have is recordings of gibberish; unintelligible and impossible to unlock.
- The only avenue for .gov actors to read communications within Signal is by infiltration into your circle, whatever that may be.
- Therefore, ONLY allow people on to the private channels that you would trust with your life. Vetting is absolutely essential. Public channels, not such a big deal. (This was a key reason why the “Oath Keepers” people were hammered by .gov, they were crawling with .gov snitches.)
- To date, this is the only viable secure messaging system that I’m aware of, without any shady ownership or technical details (like WhatsApp being owned by that paragon of virtue, Mark Zuckerfuck).
- Signal can be used for teleconferencing, sending or sharing of documents, and everything you would get from a Zoom or MS Teams platform, with the exception of online presentations. It represents a secure alternative to email platforms which may be subpoenaed by .gov agents if they go on a fishing expedition.
- Final point, set your messages inside of Signal to “disappear” after a short period of time, after which they’re permanently deleted. (Failure to have this basic security measure is the other key reason why the “Oath Keepers” people were hammered by .gov.)
I apologize to readers, for restating the same points, almost to the point of being pedantic. But taking back your privacy is the first step, and the biggest step, to fighting back against a corrupt government.

The threat that Big Brother has, able to read your emails, chats and listen to your phone calls, creates what courts call a “chilling” effect; groups can’t plan responses to tyrannical government actions without the fear that a “Fed” is listening to everything you do. That’s whole point, to keep us scared from saying what we think, organizing any kind of meaningful response, keep us scared and suspicious of our neighbors. Indeed, entire Western empire relies almost exclusively on their surveillance capabilities across the electronic spectrum.
Isn’t it time you took that away from them?!?
We need to have the ability to say what we really think, without .gov punishing us for saying what we think.
Download Signal, and take the first step… to taking back your privacy.
[In the interests of full disclosure, I have no affiliation with Signal, in any manner.]